The audit view allows you to quickly identify the IP addresses from which brute-force login attempts are carried out.
The most tell-tell sign is, that repeated login attempts were made, but never a successful login.
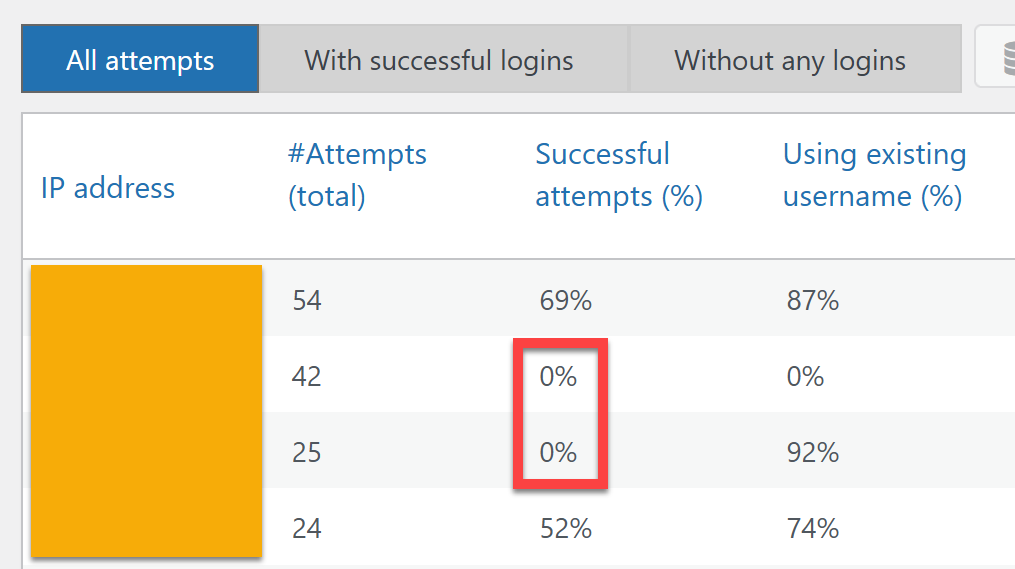
You can select those easily by using the tab “Without any logins”:
Depending on your WP Admin Audit product edition, you can then use the CSV export functionality to get a download of the malicious IP addresses in order to block them (either within WordPress or on the web server or network level).
The information “Using existing username” can also come in very handy.
However, it plays a role if your site is or is not publicly showing usernames – because the bots are smart enough to use them if they see them (e.g. as the author name of a blog post). The same obviously goes for using usernames like admin that are well-known to attackers. For this reason, those should not be used at all for live sites according to best practices.